Aquila Rey JV offers cybersecurity services designed to protect critical information assets and ensure the resilience of IT systems against evolving threats. We focus on the implementation of advanced cybersecurity frameworks, such as Zero Trust architecture, to strengthen network security and access control. Our expertise extends to certification and accreditation processes, ensuring that our clients’ systems comply with the highest standards and regulatory requirements. We employ proactive cybersecurity risk management strategies, leveraging advanced encryption and secure transmission protocols to safeguard sensitive data. Our approach includes continuous monitoring and vulnerability assessments to detect and mitigate potential threats in real-time. Additionally, we offer robust incident management and response services to address and resolve security breaches swiftly, minimizing impact and preventing recurrence. We are committed to maintaining the integrity, confidentiality, and availability of our clients’ data through a holistic and adaptive cybersecurity strategy.
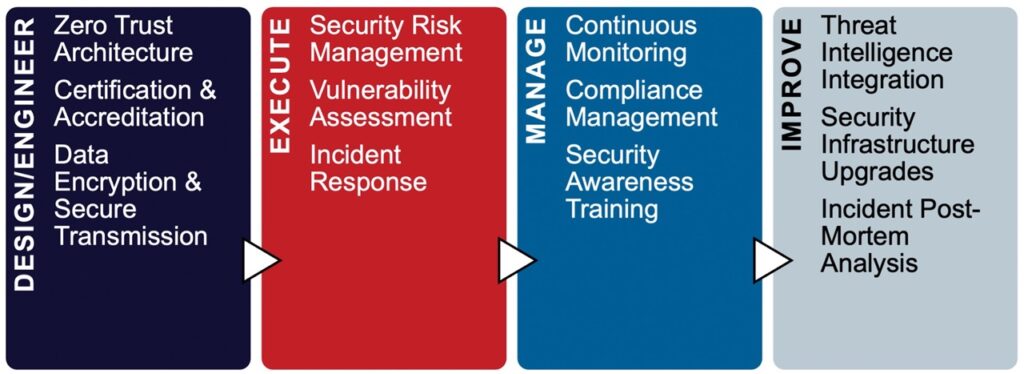
We design and implement Zero Trust architectures that enhance network security and access control by ensuring that all users, whether inside or outside the network, are authenticated and continuously verified.
Our team supports the development and submission of certification and accreditation packages to ensure compliance with stringent cybersecurity standards and regulations.
We engineer and implement advanced encryption techniques and secure transmission protocols to protect sensitive data from unauthorized access and breaches.
We proactively manage cybersecurity risks by identifying, assessing, and mitigating potential threats, ensuring the integrity and availability of critical data and systems.
Our team conducts continuous vulnerability assessments to identify and address security weaknesses in real-time, preventing exploitation and breaches.
We execute swift and methodical incident response strategies to minimize the impact of security breaches and prevent future occurrences.
We provide continuous monitoring of IT systems and networks to detect and respond to potential security threats as they arise.
Our company ensures ongoing compliance with industry standards and regulations, such as GDPR, HIPAA, and FedRAMP.
We manage comprehensive security awareness training programs to educate and empower employees to recognize and prevent potential cyber threats.
We continuously integrate threat intelligence into our security operations to stay ahead of emerging threats and adapt our defenses accordingly.
Our team regularly upgrades security infrastructure to incorporate the latest advancements in cybersecurity technology and practices.
We conduct thorough post-mortem analyses of security incidents to identify root causes, enhance defenses, and prevent future occurrences.
Aquila Rey JV offers cybersecurity services designed to protect critical information assets and ensure the resilience of IT systems against evolving threats. We focus on the implementation of advanced cybersecurity frameworks, such as Zero Trust architecture, to strengthen network security and access control. Our expertise extends to certification and accreditation processes, ensuring that our clients’ systems comply with the highest standards and regulatory requirements. We employ proactive cybersecurity risk management strategies, leveraging advanced encryption and secure transmission protocols to safeguard sensitive data. Our approach includes continuous monitoring and vulnerability assessments to detect and mitigate potential threats in real-time. Additionally, we offer robust incident management and response services to address and resolve security breaches swiftly, minimizing impact and preventing recurrence. We are committed to maintaining the integrity, confidentiality, and availability of our clients’ data through a holistic and adaptive cybersecurity strategy.






We design and implement Zero Trust architectures that enhance network security and access control by ensuring that all users, whether inside or outside the network, are authenticated and continuously verified.
Our team supports the development and submission of certification and accreditation packages to ensure compliance with stringent cybersecurity standards and regulations.
We engineer and implement advanced encryption techniques and secure transmission protocols to protect sensitive data from unauthorized access and breaches.
We proactively manage cybersecurity risks by identifying, assessing, and mitigating potential threats, ensuring the integrity and availability of critical data and systems.
Our team conducts continuous vulnerability assessments to identify and address security weaknesses in real-time, preventing exploitation and breaches.
We execute swift and methodical incident response strategies to minimize the impact of security breaches and prevent future occurrences.
We provide continuous monitoring of IT systems and networks to detect and respond to potential security threats as they arise.
Our company ensures ongoing compliance with industry standards and regulations, such as GDPR, HIPAA, and FedRAMP.
We manage comprehensive security awareness training programs to educate and empower employees to recognize and prevent potential cyber threats.
We continuously integrate threat intelligence into our security operations to stay ahead of emerging threats and adapt our defenses accordingly.
Our team regularly upgrades security infrastructure to incorporate the latest advancements in cybersecurity technology and practices.
We conduct thorough post-mortem analyses of security incidents to identify root causes, enhance defenses, and prevent future occurrences.
